The grift – part 2 (Chase credentials)
The other day I posted about a scam involving Facebook credential grifting. Last week was a great one for scam intel… I also got a scam trying to steal Chase credentials that simultaneously evolved into a scam to steal Wells Fargo credentials.
I like to describe current spam – especially phishing scams, but it works for most spam, with a hook, line, and sinker metaphor. The email hooks the victim visually, the line (a link to an illegitimate site) lures them in, and the well structured site is the sinker.
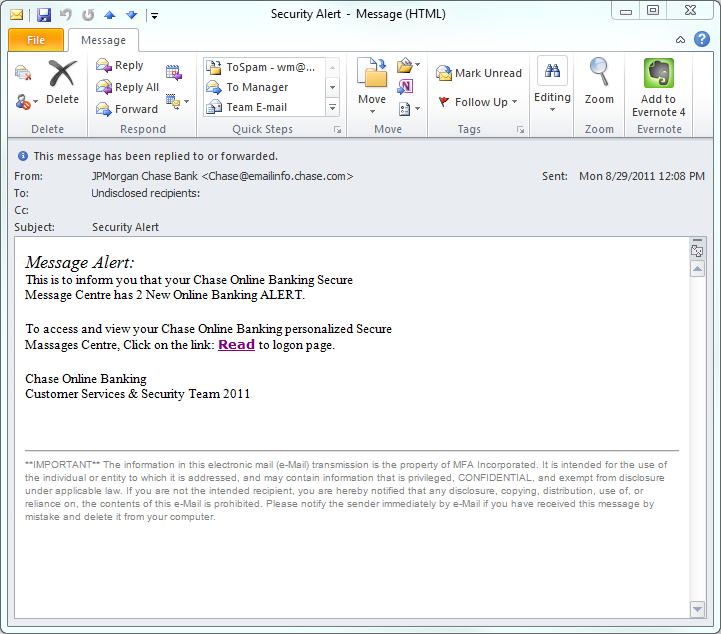
I’ve often said that too many people fall for the dancing pigs problem – in this case, they get distracted by the desperation in the email, and think, “Uh oh – if Chase emails me, I should probably check it.” Take a look at this one:
First thing to notice is it says nothing about needing to enter your credentials right away. No, this sucker is well crafted. “There’s something I need to tell you about, but it’s in your Chase alerts.” It uses HTML formatting to hide the URL, which is so blatantly not Chase, it’s good it’s invisible. After clicking, the next thing the end user sees is this page.
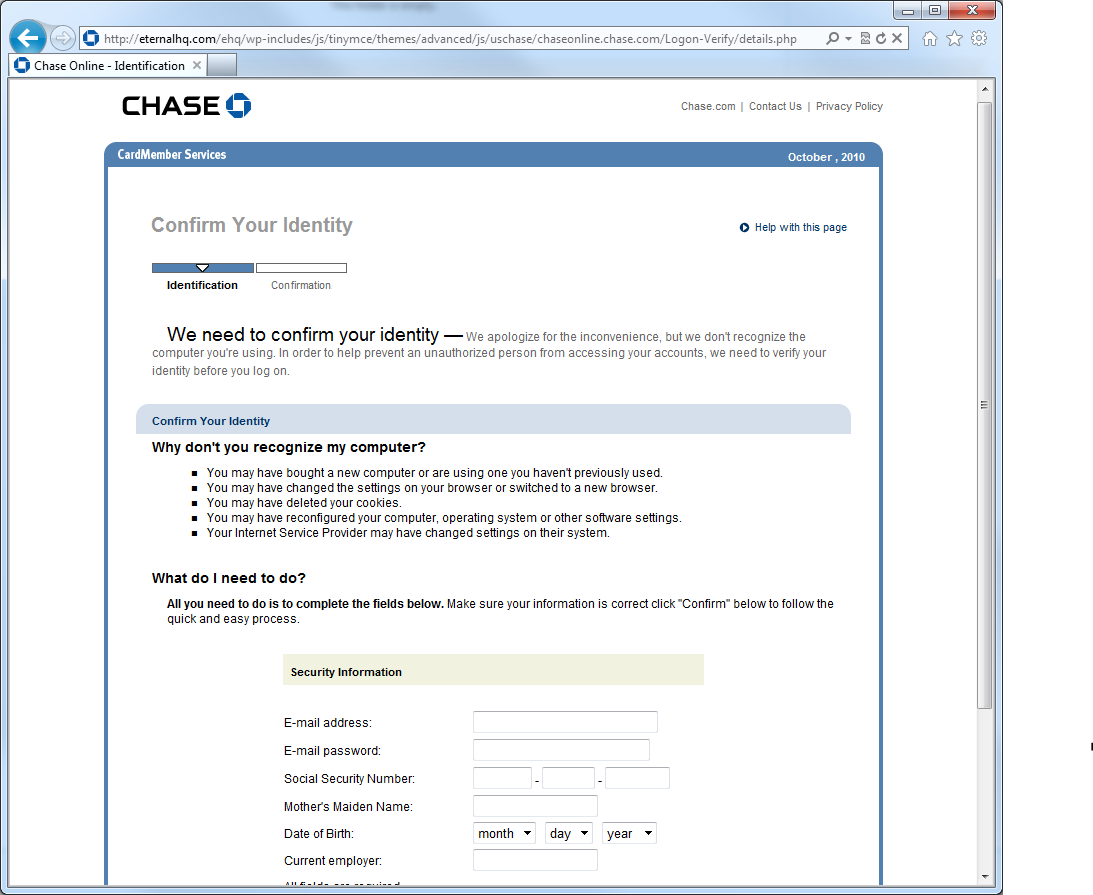
Another real gem, it looks just like Chase.com. For the typical user, who I contest never checks their address bar and rarely checks for the SSL “lock” icon (the URL and the lack of SSL should both indicate to the end user that this site reeks of crime). But of course, this is about my Chase alerts, and my mind is single-tracking on that. So I put in my credentials and click Log On.
I’m sunk. But wait, it gets worse. Check out this beauty that shows up next.
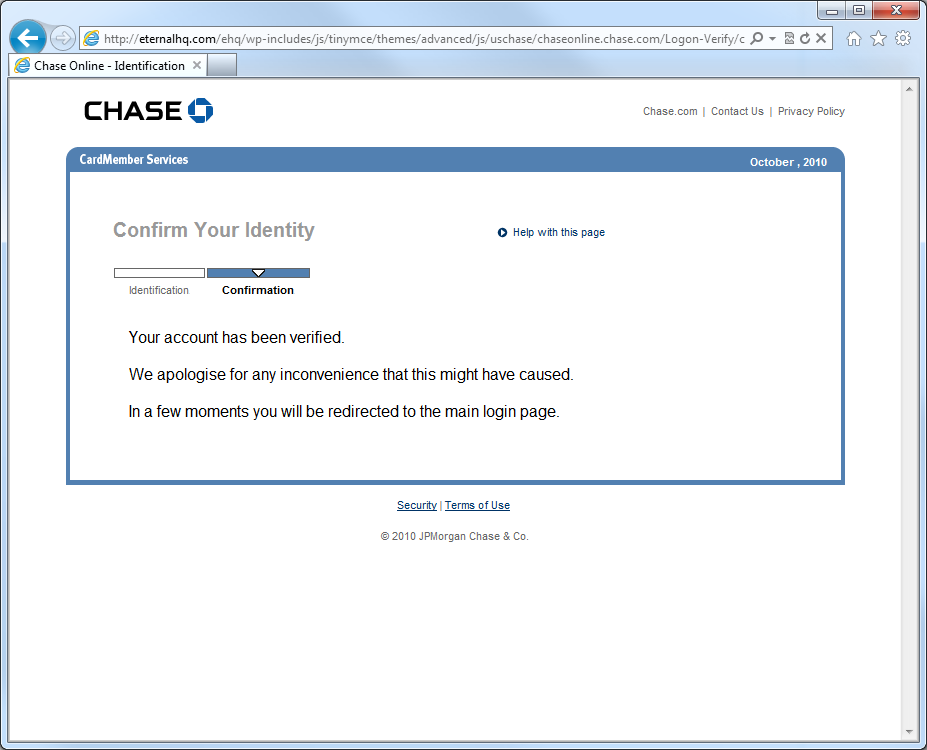
Yes, that’s right. These guys have crafted this to look like Chase’s “I don’t know this computer” page, which never asks for this kind of information. This isn’t just credential phishing, this is identity theft.
Of course that page does no error handling, so it was pleased as punch to accept the bogus info I put in, and then redirect me to Chase.com.
It’s as if I had fixed all of the problems and now I could really log on and read the alerts I had originally clicked the link in order to see.
This scam was especially sleazy because it used a reasonably legitimate looking site in Korea that had obviously been compromised (BBS/forum software) to perform a quickie client-side redirection to this second URL, which is running under the guises of a compromised TinyMCE running inside of a seldom-used WordPress blog on this site. So one compromised site hosts the redirector, and another compromised site hosts the phishing collection pages. Lovely. The phishing pages initially were hosted on another domain, but when I informed them, they fixed it. The grifters had obviously gathered enough compromised sites to simply switch their redirector (whose admin has failed to fix their site after two notifications) to point to this new site, which has not addressed their issue yet, after being informed. After being grifted, as I noted, the victim is courteously redirected back to Chase.com, which is of course now the right URL and SSL.
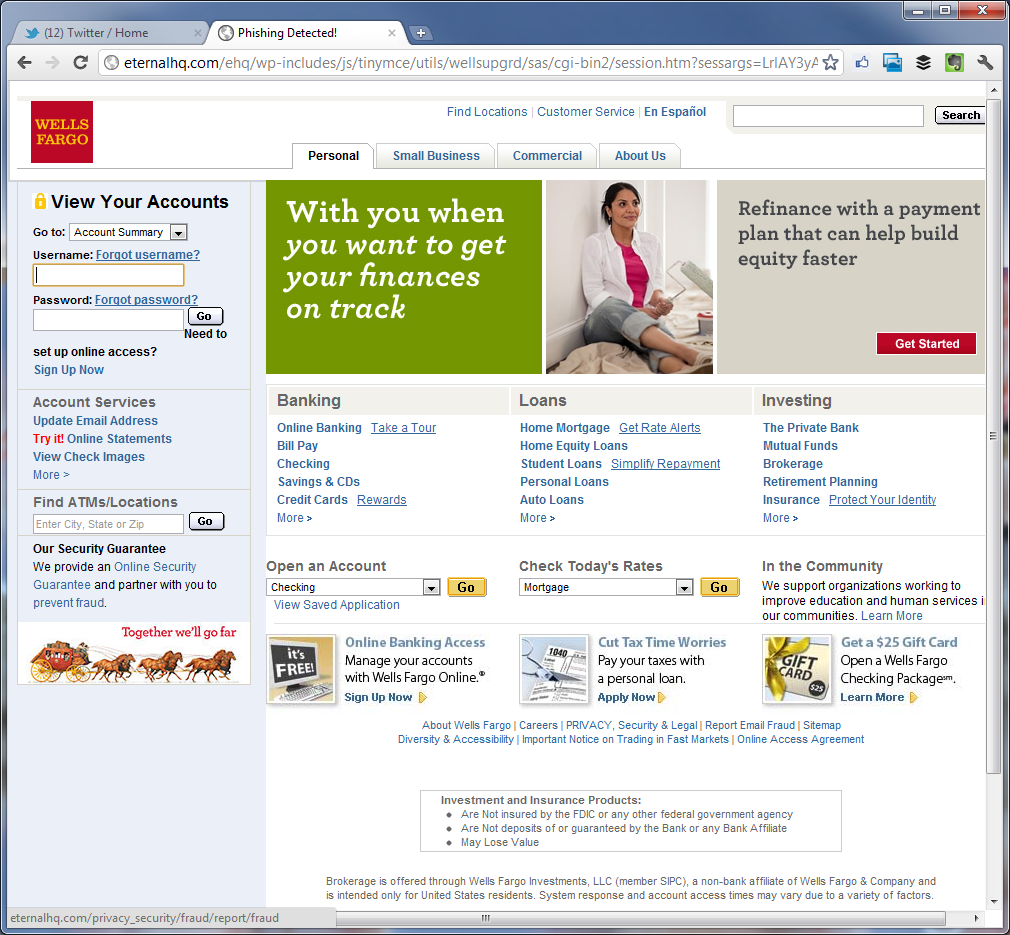
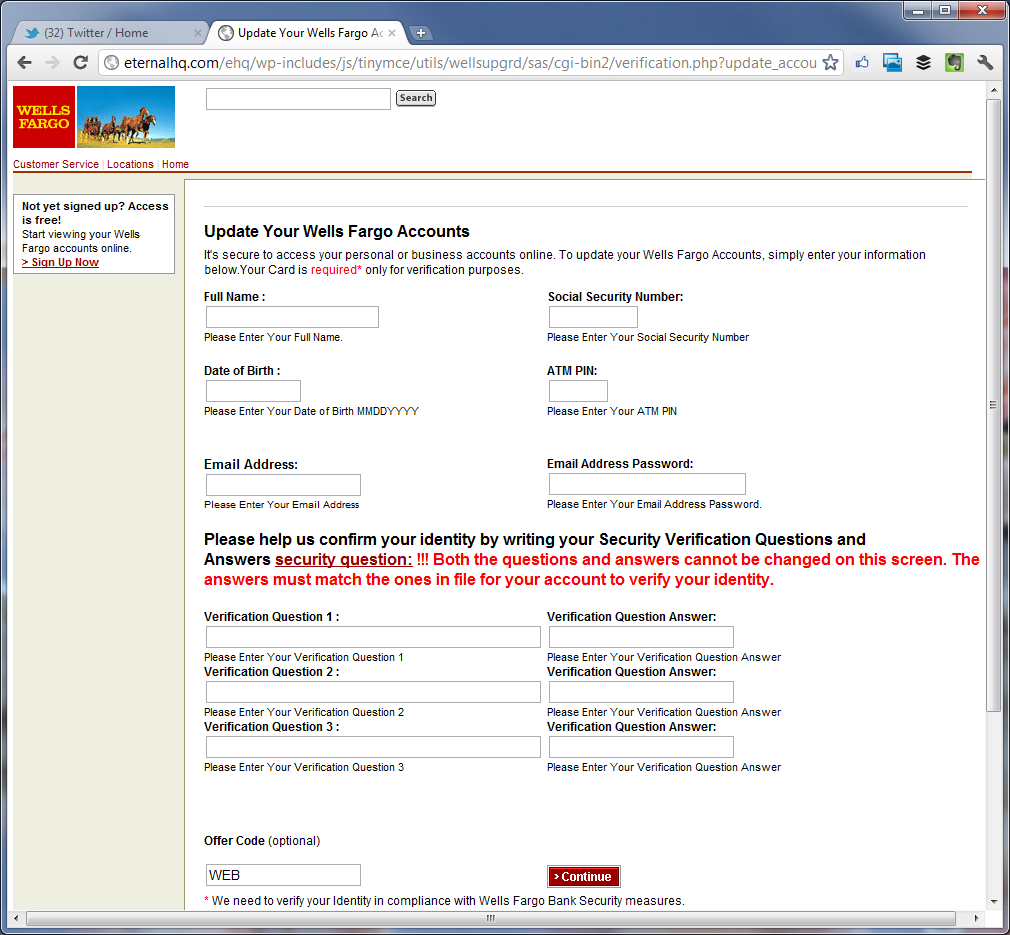
I mentioned it evolved to be a Wells Fargo grift too. Same MO, same compromised domains.
Line:
Sinker:
We live in an era when the browser must protect users from phishing better than this. Chrome caught these, but only after they had been in the wild for a few days.